Windows Internals
1. Windows API
The Windows API provides native functionality to interact with key components of the Windows operating system. The API is widely used by many, including red teamers, threat actors, blue teamers, software developers, and solution providers.
The API can integrate seamlessly with the Windows system, offering its range of use cases. You may see the Win32 API being used for offensive tool and malware development, EDR (Endpoint Detection & Response) engineering, and general software applications. For more information about all of the use cases for the API, check out the Windows API Index.
Programs often need to access or modify Windows subsystems or hardware but are restricted to maintain machine stability. To solve this problem, Microsoft released the Win32 API, a library to interface between user-mode applications and the kernel.
Windows distinguishes hardware access by two distinct modes: user and kernel mode. These modes determine the hardware, kernel, and memory access an application or driver is permitted. API or system calls interface between each mode, sending information to the system to be processed in kernel mode.
No direct hardware access
Direct hardware access
Access to "owned" memory locations
Access to entire physical memory
Below is a visual representation of how a user application can use API calls to modify kernel components.
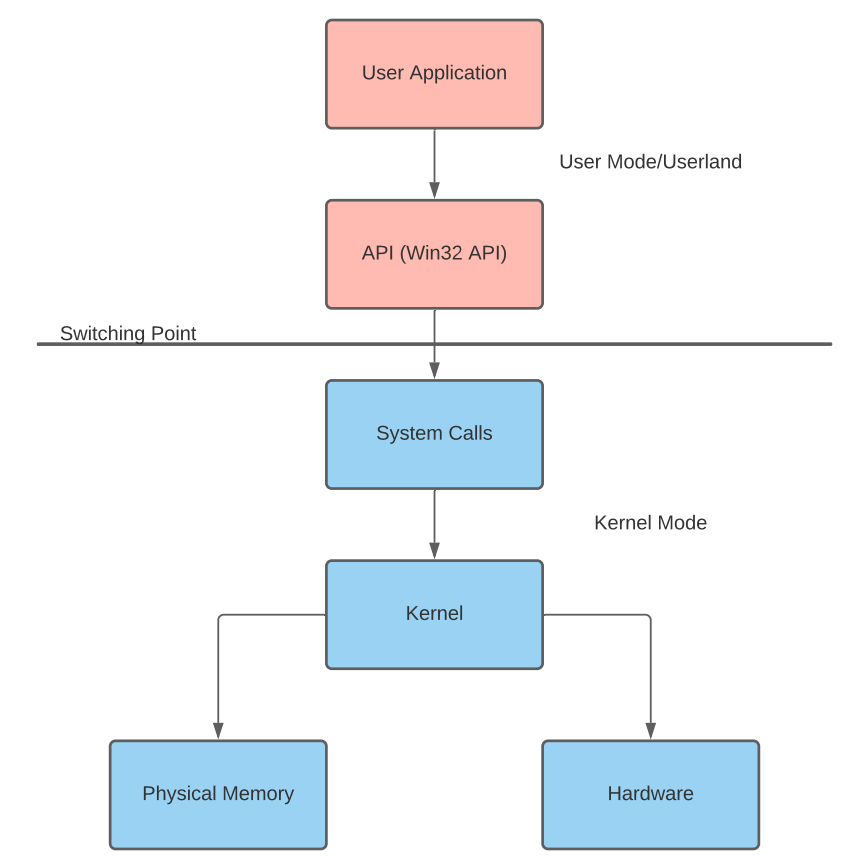
When looking at how languages interact with the Win32 API, this process can become further warped; the application will go through the language runtime before going through the API.
Notes: we access the resources of system using api via system calls using win32 api. win32 api uses user32.dll or kernal32.dll according to the user or kernal mode which used to call the api. For example we can get system information using systeminfo() api.
2. Abusing Windows Internals
Last updated