16. Additional Capabilities of Address Sanitizer
Exercise 16: Exploring Additional Capabilities of Address Sanitizer
Lab Tasks
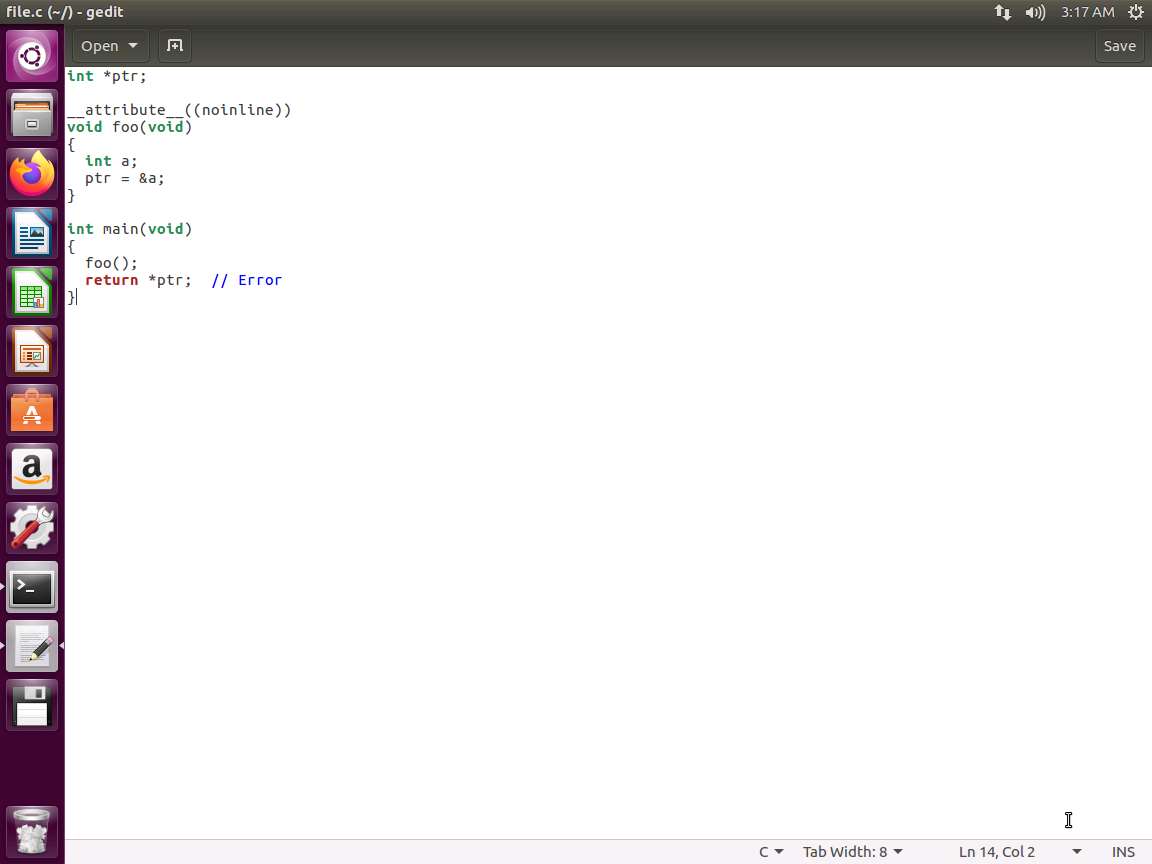
Screenshot 
Screenshot 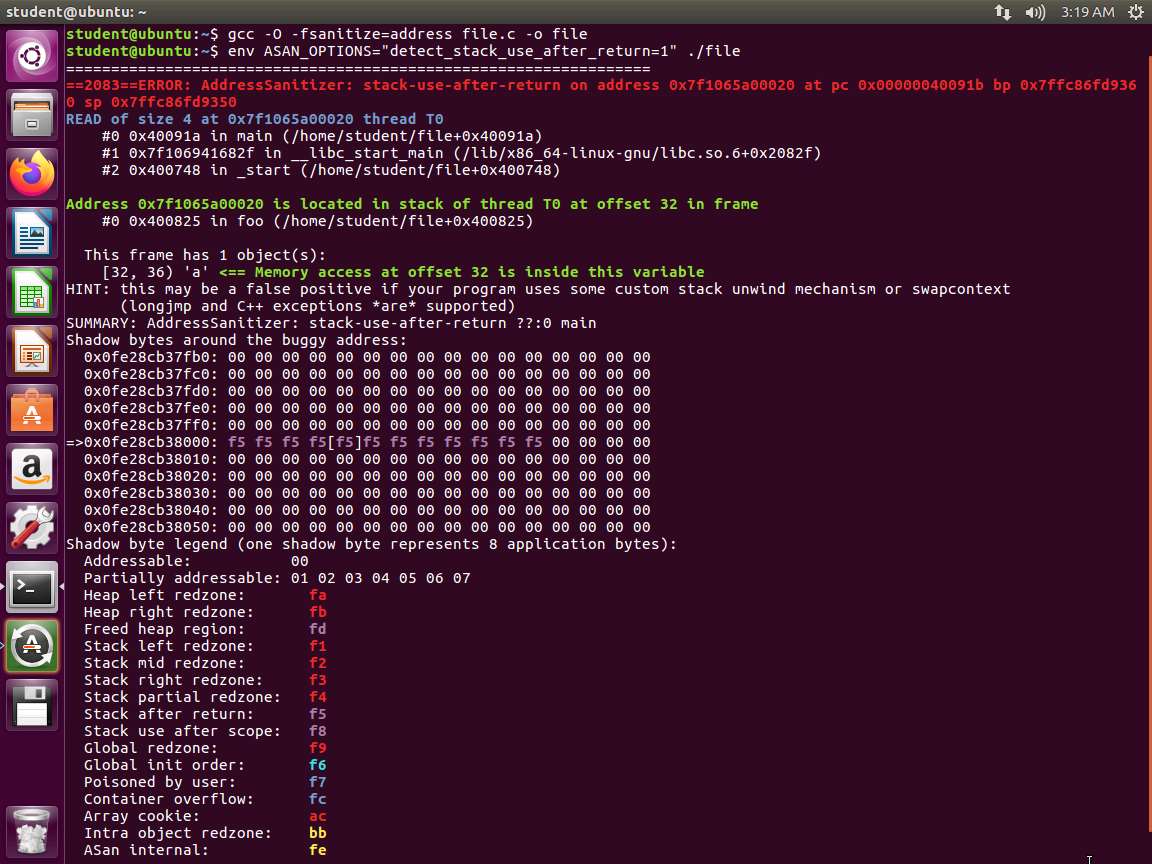
Screenshot
Previous15. Fuzzing an Application with American Fuzzy Lop (AFL) and Capstone FrameworkNext17. Fuzzing an Application with Peach Framework
Last updated